Use ZAP tool to intercept HTTP Traffic
ZAP Tool
Zed Attack Proxy is one of the most popular security tool that used to find security vulnerabilities in applications.This blog discuss how we can use the ZAP tool to intercept and modify the HTTP and HTTPS traffic.
Intercepting the traffic using the ZAP tool
Before we start, lets download and install the ZAP Tool.
1) Start the ZAP tool using / zap.sh
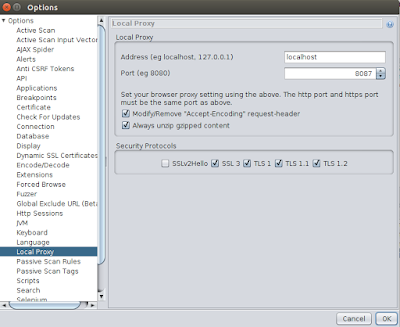
2) Configure local proxy settings
To configure the Local Proxy settings in the ZAP tool go to Tools -> Options -> Local Proxy and provide the port to listen.
3) Configure the browser
Now open your preferred browser and set up the proxy to listen to above configured port.
For example: If you are using FireFox browser browser proxy can be configured by navigating to "Edit -> Preferences -> Advanced -> Setting -> Manual Proxy Configuration" and providing the same port configured in the ZAP proxy
4) Recording the scenario
Open the website that you want to intercept using the browser and verify the site is listed in the site list. Now record the scenario that you want to intercept by executing the steps in your browser.
5) Intercepting the requests
Now you have the request response flow recorded in the ZAP tool. To view the request response information you have to select a request from the left side panel and get the information via the right side "Request" and "Response" tabs.
Next step is to add a break point to the request to stop it to modify the content.
Adding a Break Point
Right click on the request that you want to add a break point, and then select "Break" to add a break point
After adding the breakpoint. Record the same scenario that you recorded above. You will notice that, when the browser reached to the intercepted request it will open up a new tab called 'Break'.
Use the "Break" tab to modify the request headers and body. Then click the "Submit and step to next request or response" icon to submit the request.
Then ZAP will return the request to the server with the changes applied to it.




Good stuff
ReplyDelete